Schutz des Unternehmens und Ihrer Mitarbeiter vor Cyberbedrohungen
What is MTD?
MTD of Mobile Threat Defense is an option that protects your end users' smartphones against potential cyber-attacks and threats. Fraudsters try to obtain personal information via text messages, email, social media or applications. Through the MTD app, your end user's smartphone is protected from attacks that can affect the network, system or applications. Are you looking for a manual for your end users? You can find it at www.proximus.be/mtduser . Through the MTD portal, you as an administrator have access to a secure platform where you can set the option for your end users, set company policies and manage threats as they arise.
Would you like more information? As administrator for your company, you can contact Proximus contact or partner . They will first discuss with you how the MTD option can be added to your mobile contract and then provide you with all the documents needed for activation.
Accessing the portal
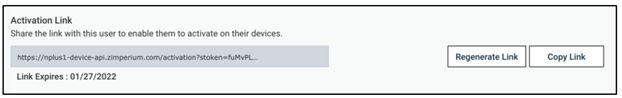
After activation of the MTD option, a welcome email is sent to both the end users and the administrator(s) of the mobile contract. As an administrator, you can use the welcome email to activate and install the MTD app on your own device on the one hand and activate your account on the MTD portal on the other. Want to know how to get started with the MTD app on your own device? Read our user instructions to protect your smartphone from scams .
To activate your account on the MTD portal as an administrator, you will need the welcome email. You will receive it at the email address you provided on the order form. If you have not received an activation email, please check your spam or junk folder.
Did you receive the activation email? Keep it at hand, we'll explain what you need to do:
- Open the welcome email on your PC.
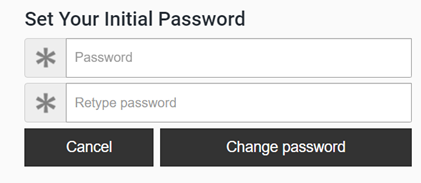
- Click on the link in the email and request a reset of your password through the MTD portal. Please note you need to choose a new password within 24 hours of receiving the email.
- Enter your newly chosen password and confirm it a second time.
- Using the Portal link, you can now access the MTD portal with your email address (USERID).
Get started as administrator
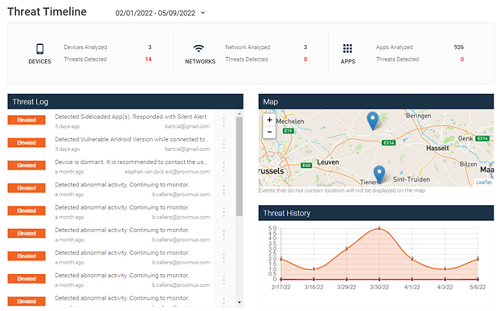
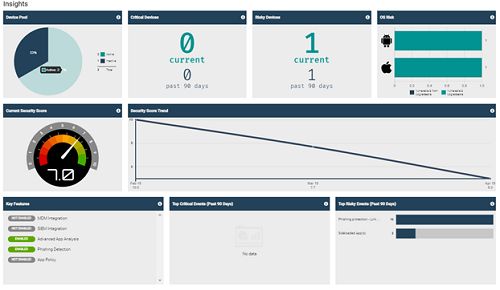
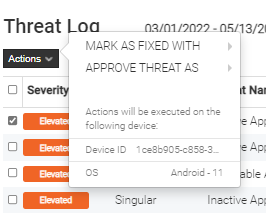
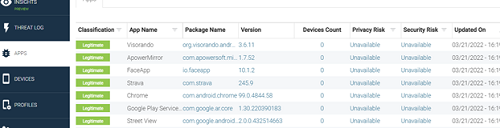
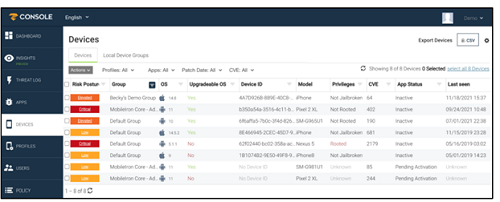
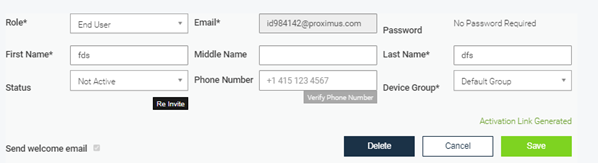
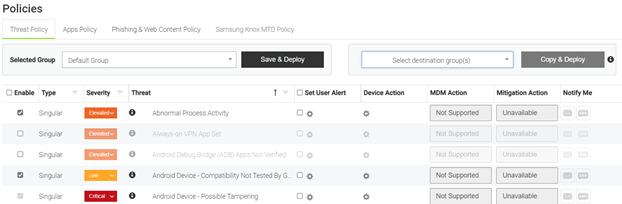
Through the MTD portal, you can access dashboards and reports from the end users for which the MTD option is active. The portal also allows you to configure your organization's security policies. You can download the user manual in Dutch(PDF, 3 MB, auf Niederländisch) or French(PDF, 3 MB, auf Französisch) or do you prefer a concise explanation? Below we list the main features of the MTD portal: