Can no password be more secure than a complex one?
Published on 07/06/2021 in Bits & Bytes
Passwords – we all have too many of them and we frequently forget them. We end up reusing the same password over and over again and this is extremely unsafe. Password manager systems can help, but passwordless authentication is a better alternative.

Passwordless authentication has been around for some time now, but there is still a lot of confusion about the concept. Stephan Van Dyck, Cyber Security Consultant at Proximus, explores the nature and history of passwords and answers the burning questions about passwordless authentication.
History of the password
The concept of the password long predates the computer. Passwords have been used for thousands of years as a form of authentication. The Roman military, for instance, used passwords to distinguish enemies from allies.
In computer science, passwords were introduced in the 1960s by MIT researcher Fernando Corbato. The modern password serves the same purpose as the ancient one: to protect confidentiality. Although far from perfect, it became the go-to method for computer security because of its simplicity.
Do you want to learn more about how to get started with passwordless authentication and/or risk-based conditional access? Talk to one of our experts.
What are the issues with passwords?
Passwords have many weaknesses, some of which have been around for decades. Let’s zoom in on a few of them:
- Password guessing
- Weak hashing algorithms
- Logical passwords
- Default passwords
- Reused passwords
- Leaked credentials
- Brute force attacks
- …
There are many different ways that an attacker can abuse passwords. One of the most common vulnerabilities is the fact that people use passwords that are easy to remember, such as the name of their pet, partner, favorite sports team, the word “password”, etc.
To address these issues, companies have tried to make password creation more complex by requiring the use of capital letters, special characters, numbers, and a minimum number of characters, and by preventing the reuse of old passwords. Although well intentioned, this hasn’t solved the problem as people still try to use logic to remember their passwords. One of the very worst habits? Using the same password for different applications.
Let us look at an example.
Let’s say your password is the word “secret”, but to comply with the new security policy you need to rethink your favorite password. Most people will do the following:
- To comply with the capital letter requirement, nine out of 10 people will put the capital letter at the beginning of the word. In our example we would get “Secret”.
- If they’re required to add a number and a distinctive character, they will probably place it all the way at the end, so we would get “Secret1!”.
- To make things worse, if there is a history policy, the password might become sequential: Secret1!, Secret2!, etc.
If you are smiling while reading this, chances are you have also used this technique (most people have). Hackers are, of course, also aware that most of us are doing this, so guessing becomes very easy. When people use the same easy-to-remember password for multiple accounts, hackers can guess the password and breach multiple accounts in no time.
Multi-factor authentication to the rescue
Multi-factor authentication (MFA) helps to solve many vulnerabilities linked to passwords. MFA combines something you know (a password) with something you have (an authenticator app, a token, a certificate) or something you are, usually some form of biometric identification (a fingerprint, iris scan, face recognition).
While MFA addresses most weaknesses, we are still stuck with the password: it remains the first form of authentication and, as we covered earlier, it is one of the biggest sources of frustration in our lives. Passwords usually aren’t user-friendly or secure and they are the number 1 reason why people call the IT helpdesk.
Isn’t there a better way?
Yes, there is! The key to being safe is passwordless authentication in combination with risk-based conditional access.
Instead of using a password as the first step in the authentication chain, we usually start with “something you have” such as a certificate, token, or a smartphone with an authenticator app. You can find a demo of how this works below. This removes the option for a hacker to guess or “brute force” the password and stops an attack before it can even happen.
Combine this with “something you are” (i.e. biometric identification), such as a fingerprint or facial recognition, and you get a much stronger multi-factor authentication flow. When you also add risk-based conditional access to the authentication process, you get an even more secure solution because of the added context.
The concept of conditional access is that context is added to the authentication request. Details about device health, user behavior, location, source IP address, operating system, and browser give great insight into the legitimacy of an authentication process.
Let us look at an example:
- Megan works in the finance department of company ABC and she wants to access the finance department’s SharePoint. Megan’s usual routine is to use a Windows 10 corporate laptop connected to the company network and Microsoft Edge as the browser. She normally starts her workday between 8:00 a.m. and 10:00 a.m. and finishes between 4:30 p.m. and 6:00 p.m.
- One day, the company ABC SharePoint receives an authentication request from someone claiming to be Megan. The request comes from a Linux machine using Tor as its browser in the middle of the night on a Sunday. We can immediately see that this is odd behavior for Megan and we may want to further investigate this authentication request.
As we can see, context helps IT teams to build more granular access policies and permit or deny access on based on a risk assessment.
So passwordless authentication in combination with risk-based conditional access not only improves security by addressing weaknesses, it also enhances the end-user experience by removing all the frustrations linked to passwords.
Demo passwordless authentication
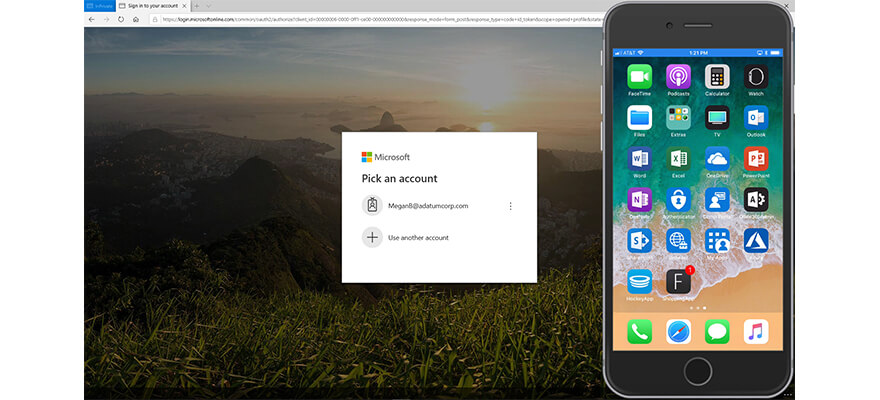
Megan is trying to access her professional Office 365 environment using a personal PC (not managed by the company). You can also see Megan’s smartphone which has the Microsoft Authenticator app provided by Adatum Corp installed.
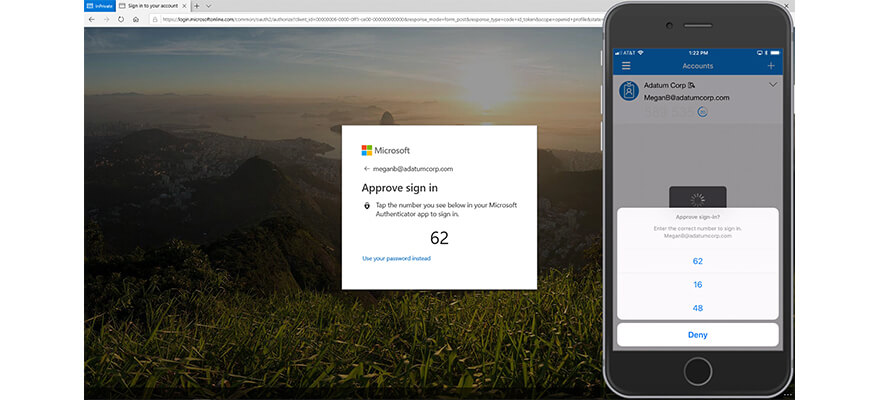
When Megan enters her email address, she receives an authentication challenge pop-up on her smartphone. Megan has to type the number she has received into her PC. This challenge ensures it is Megan who is trying to log in.
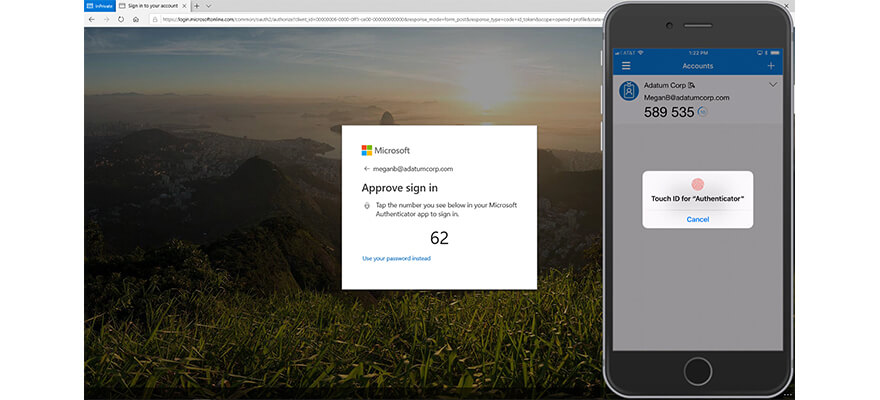
In the second step of the authentication process, Megan must prove it is actually her trying to log in and not someone who stole or found her smartphone. Megan uses her fingerprint (biometrics) to validate the request.
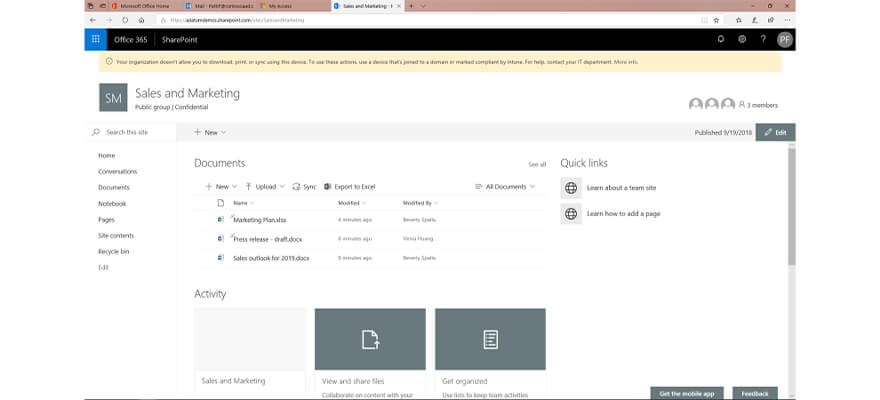
Megan has passed all checks (we can confirm it is her), so she gets access to the corporate resources without using a password.
In this demo the verification process was done based on “something she has” (the smartphone with the authenticator app) and “something she is” (her fingerprint using biometrics).
Stephan Van Dyck is Cyber Security Consultant at Proximus with a strong focus on workplace security, including endpoint security, endpoint management, identity management, and Microsoft 365. He is CISSP certified. Stephan conducts security assessments for clients and helps them to improve and implement their security strategy.
Experts
Our experts keep you informed on the latest news and trends for ICT professionals.