How do you protect your data in Office 365?
Published on 31/12/2020 in Tech, tips & tricks
From mobile devices over the cloud to SharePoint: your company data is everywhere. Keeping it secure is almost impossible. Or perhaps not: your Office 365 data protects you with Data Loss Prevention (DLP) for endpoints in the Microsoft Compliance Center.

Data security: top priority
E-mails, text messages, documents: your company generates great amounts of data every day. Because of COVID-19, this is not longer just inside your company, but also in your employees' homes. In other words, the boundary between business and private life has become wafer-thin. Securing your data is therefore more than ever the core of your security policy. A policy that revolves around Zero Trust: you cannot and should not trust anything or anyone anymore.
You remain responsible
Make no mistake: even if you use SaaS applications that place part of the responsibility with your cloud provider, you remain responsible for the classification of your data. And that is where Data Loss Prevention (DLP) comes into play: it closes the gap between the classification and the security of your data. DLP for Microsoft endpoints is a failry new but promising feature that actually works.
Wish to find out more about DLP for endpoints in Office 365? Watch the webinar.
Know, protect and manage your data
Information security consists of three pillars. You need to know, protect and manage your data. That first pillar alone is a real challenge. Do you know where all your data is located? Probably not, because we generate so much data every day that it is impossible to track. With DLP cloud solutions you know where your data is stored and who processes it where and when.
The security of your data – your intellectual property, the privacy of your employees and the information you generate – is the most important pillar. You protect it by taking the right security measures. And by managing your data – the third pillar – you know exactly when it is where.
Secure mobile devices with DLP
Data security is all about the confidentiality and integrity of your data. Your customers' personal data is stored on mobile devices. Thanks to the security measures we use to protect this data, it remains confidential. With DLP for endpoints, we can make that data extra secure. This gives us full control over it and closes the gap that still exists in data security on mobile devices.
Classification: insight into your data
Secure your endpoints in the Microsoft Compliance Center. ‘Data classification’ gives you an overview of all types of sensitive data you keep and all sensitivity and retention labels you use in your company. Microsoft has already defined 153 data types that recognize most types of local and regulatory sensitive data. If that is not enough choice for you, you can create new data types yourself.
Down to the smallest detail
Under the 'Content explorer' tab you can see how many documents and hits the Compliance Center finds in your company per data type. If you look further, you can also see which documents contain these sensitive data types and who created them. You will also find the retention labels of the documents and other types of sensitive information found in the documents.
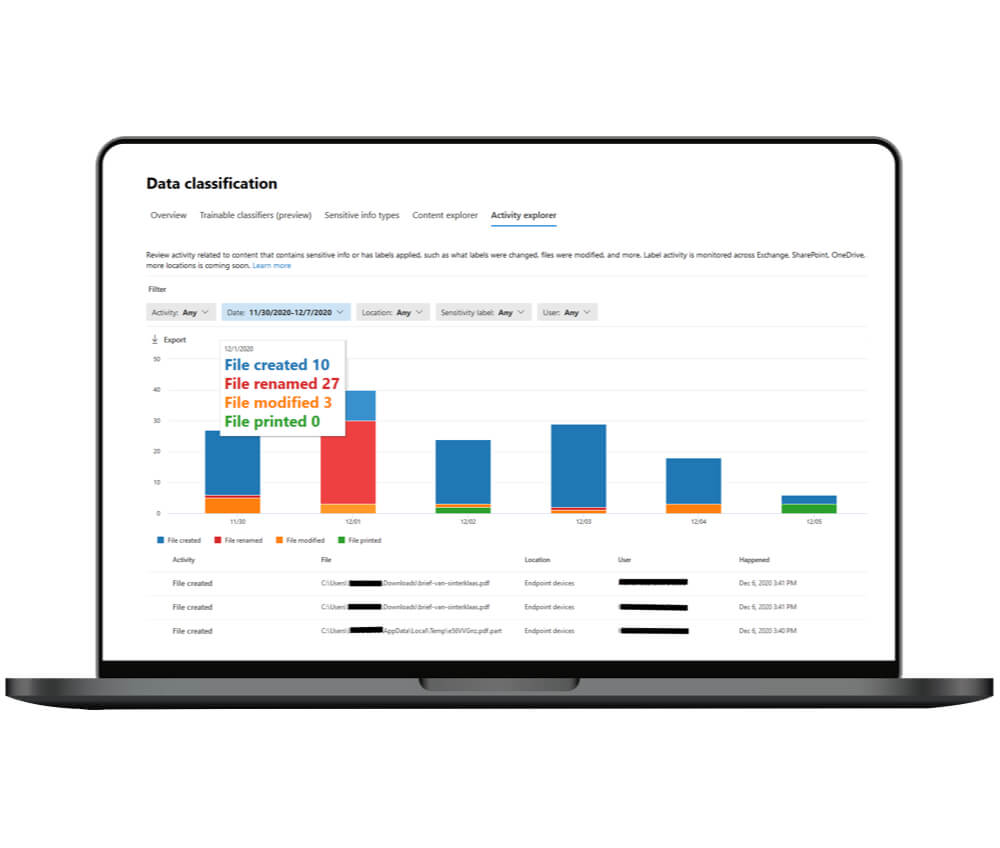
Under the tab 'Activity explorer', you can see what your employees do with those documents on a daily basis. For example, the number of new and deleted labels, the number of copied, modified and printed documents, and so on. This way you get an idea of what levels of protection your company needs. This overview can also be requested per sensitivity label, activity or location.
Protect your data
To protect your data, go to 'Policies' in the Compliance Center and choose the 'Data Loss Prevention' policy. There are already a few DLP policies defined in the Compliance Center policy series. You do not need to create a new policy, just add endpoint DLP to an existing policy and choose where to apply it. For example for data stored in SharePoint, OneDrive, Teams, ... This is also where you add your devices. Instead of protecting all devices, you also protect the devices of specific users or of a specific group.
Edit your security policy
The next step: the rules of your policy. These determine what happens when certain content is detected. First, you will again see the types of sensitive information that are detected in the policy. An action has already been defined: if an employee wants to share information from the 365 services with someone outside your company, the policy will take effect and the sharing will be blocked.
Three security measures
Using ‘Add an action’, you can add endpoints and actions to a line yourself. You will then see what you are going to do, namely: Audit or restrict activities on Windows devices. You will get a series of possible activities for which you can set three security measures each: audit, block or block and override. When you really want to protect your data, you choose blocking. Because overriding means that your employees can explain why they take that action and then just continue. If so, your data officers and security administrators will be notified.
Set up notifications
You can also set which users will be notified in the event of an infringement. You then have the choice to have Microsoft's standard notification appear or to enter your own text. You can also determine the seriousness of the infringement. And last but not least, you have the possibility to test your policy first or activate it immediately.
Four security measures
The 'Endpoint DLP settings' are general settings that apply to each policy. You can choose from four security measures:
- Exclude file locations
- Unauthorized file sharing apps
- Unauthorized browsers
- Block or allow domain names or service domains
Consequences for your employees
How do your employees experience this security? As soon as they breach a security measure, think of printing a file or copying it to another folder, or copying and pasting data from a document, a pop-up appears. This will explain to them that Data Loss Prevention is applied and that they cannot do what they are attempting to do.
And have you activated any unauthorized apps or browsers? If so, they will be blocked immediately when opening and your employees cannot override this. By default, only Edge is allowed as a browser because it is the only one that meets Microsoft's information security requirements.
Would you like more information about security for your company?
Experts
Our experts keep you informed on the latest news and trends for ICT professionals.